Can the government read my text messages?
There's a meme that every person has a U.S. government agent assigned to read their text messages. That’s not true. But government agencies, from the National Security Administration to local police departments, can potentially read the conversations on many text messaging applications. Fortunately, this is not always the case, and there are many ways you can protect your privacy.
Here's how it works
Text messages—also known as SMS, MMS, or RCS messages—aren’t usually encrypted. When a message is not encrypted, it means your phone company can and will often store a copy of conversations. These stored conversations can then be requested by law enforcement with a subpoena. Agencies like the NSA can capture and store messages as they travel over the network, or any number of law enforcement agencies can employ technologies like cell-site simulators to capture messages.
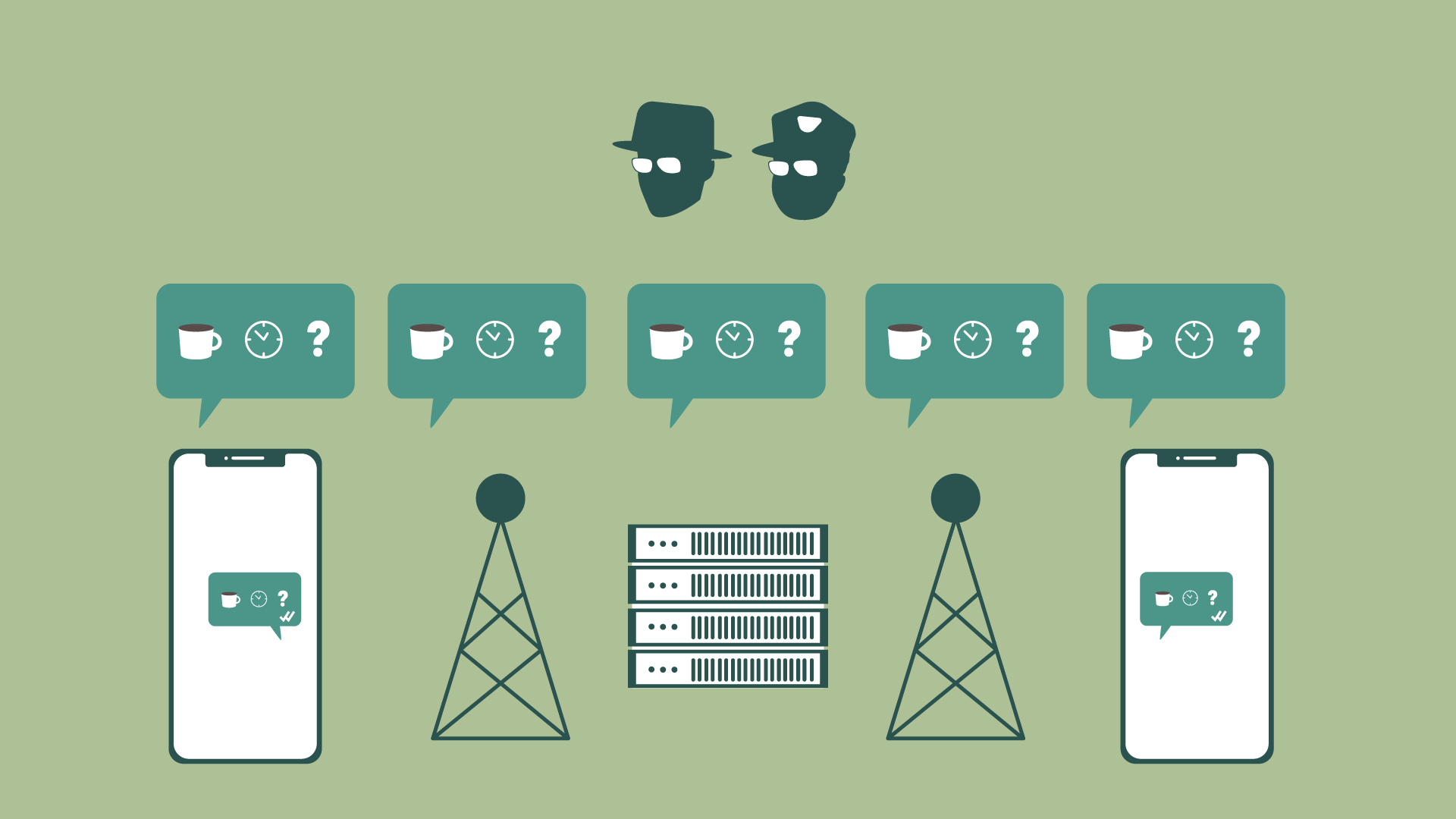
Encryption cloaks your conversations using complex math so that if these agencies and companies do look at them, they only see garbled, unreadable text. If the contents of your chat are end-to-end encrypted, they can’t be read by your phone company, snooped on by the NSA, or accessed with a subpoena.
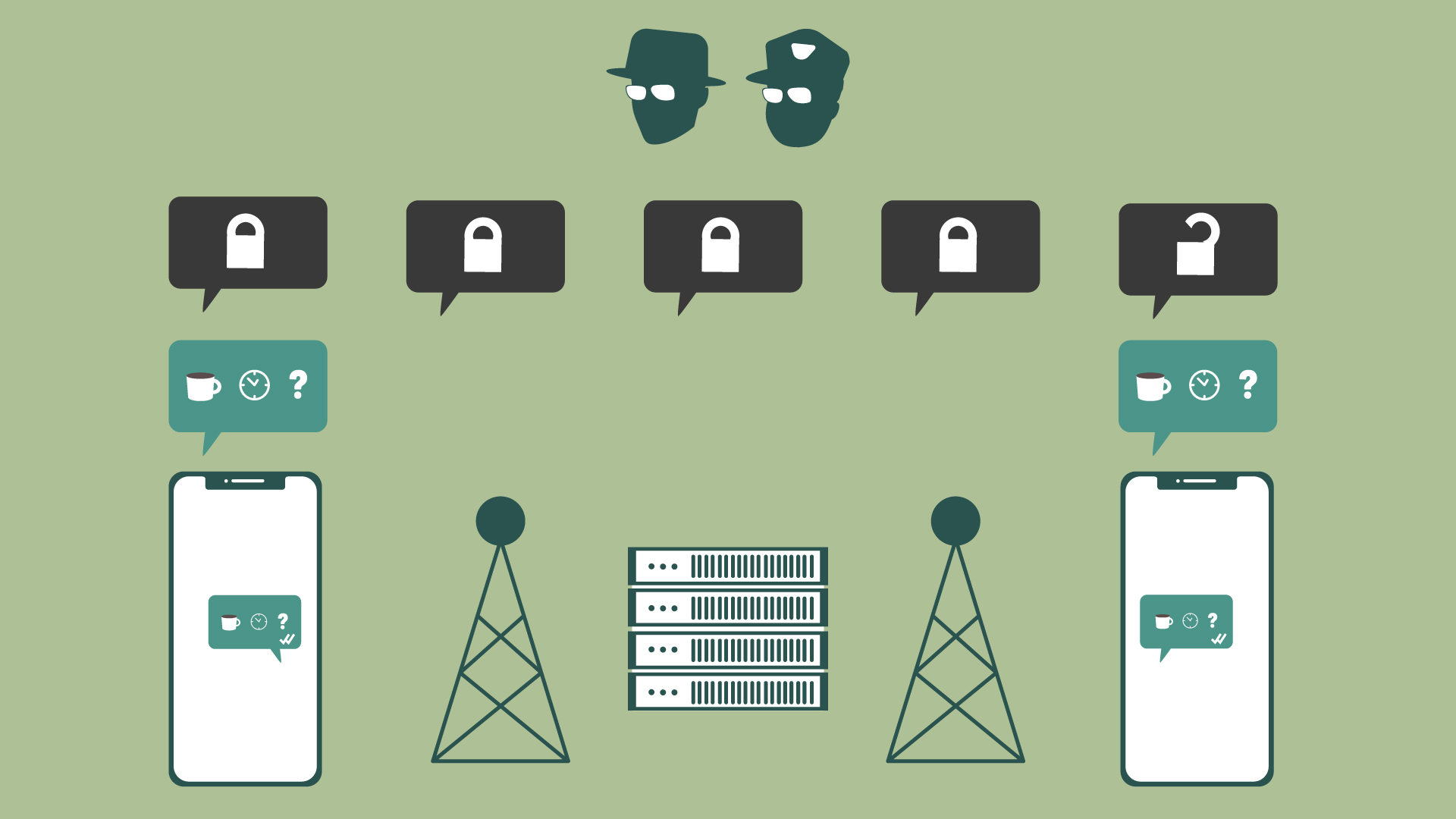
Some messenger apps will indicate if they’re end-to-end encrypted: iMessage with a blue chat bubble is encrypted, whereas a green chat bubble means it’s not encrypted, and Google Messages are encrypted if you see the lock icon. But other messenger apps, like Signal, WhatsApp, and Facebook Messenger, are end-to-end encrypted by default.
Some people believe governments must possess special tools to break modern encryption methods at scale, but there is no evidence that this is true, and it is mathematically unlikely, if not impossible. This is why EFF recommends you always use end-to-end encrypted messaging whenever possible.
Unfortunately, encrypted messaging can’t stop every way the government can read your text messages. If someone has physical access to your unlocked phone, as can happen during an arrest, then that person could read all of your encrypted messages the same way you can. In the United States, using a biometric option—like your face scan or fingerprint—to unlock your phone may also compromise legal protections for the contents of your phone afforded to you under the Fifth Amendment privilege against compelled incrimination. But under current law, which is still in flux, using a memorized passcode generally provides a stronger legal footing to push back against a court order of compelled device unlocking/decryption.
Even if your phone isn’t unlocked, police have several tools to try to unlock your phone and read your encrypted messages, including Cellebrite and Greykey devices. If an agency cannot get physical access to your phone, they could also try to remotely plant spyware on your phone, which could give them full access to everything, including encrypted messages.
You can defend against these types of attacks by having a strong lock screen password for protection against physical searches, and by keeping your phone up to date with the latest software. You can also turn on disappearing messages for any chat app that supports it. This way, if someone does get access to your phone (or puts malware on it), they will not be able to see older messages. These precautions also extend to your contacts who receive your messages: Helping your friends to be more security-minded with their devices makes our communities more protected, too.
One final way law enforcement can use to read your text messages is to get a backup of them from your cloud provider, like Apple or Google, as the backups are often stored unencrypted by default. We recommend that you either do not use backups, enable Advanced Data Protection for iCloud if you have an iPhone, or enable encrypted backups in apps like WhatsApp if you are worried about the government reading your messages.
Why this needs to change
In many areas of our lives, privacy can be difficult to find. Local governments are installing increasing numbers of cameras, license plate readers, and other technology. Schools and workplaces frequently use monitoring software to track web browsing, communications, and even productivity. As our lives become increasingly digital, it's more and more common for companies to collect and share detailed information about us, often without our knowledge.
But private communication is one place where we can, and must, protect ourselves. For some groups, such as minorities that are targeted by the government, the consequences of intercepted communications are very dangerous. Privacy is a human right, and the ability to have a private conversation is foundational for many of our other rights.
What you can do
Use (and Encourage the Use of) End-to-End Encrypted Messaging Apps:
Avoid using chat apps that aren’t end-to-end encrypted when you can (like standard SMS messages, as well as apps like Discord or Slack, amongst others), and restrict all sensitive communications to encrypted chat apps.
Turn on disappearing messages. Here’s how to do that on Signal and WhatsApp.
Use a strong lock screen password on your phone and turn off biometric unlocking if you are in a situation where you could be arrested, like a protest.
If keeping your conversations private is important to you and your friends, encourage your contacts to use end-to-end encrypted apps too!
Learn More about Metadata
Just because the contents of your messages are encrypted, other information may be visible, such as who you are communicating with and when. Understand what information is available in your metadata.
EFF has your back
The Electronic Frontier Foundation works to defend your digital privacy. Our non-profit organization of lawyers, technologists, and activists build privacy protecting tools and fight in court, in Congress, and across the country to ensure that your communications are protected from unconstitutional searches, government agency spying, and technical backdoors. Over the last thirty years, we’ve won important protections for your privacy, free speech, and innovation rights. Learn more about our work here.